Cyber Security Risks In Social Media Banking

Social Media is the most used platform on day-to-day basis by millions of people around the world.
Social media banking is the usage of social platforms such as Facebook, twitter, WhatsApp for Marketing, communication, for collecting feedback and reactions and to perform Banking Operations such as Transactions, Account summary and status enquiry, etc. We have observed using social media as a platform in 2 ways.
1. Non-Banking Operations – Marketing, Branding, Feedback, Business Analysis.
2. Banking Operations – Transactions, Communications and alerts, Account summary, status of the account or cards, reporting fraud/stolen card details etc.
Use cases of Social Media Banking:
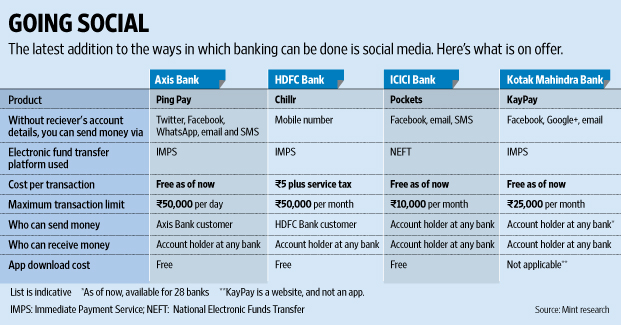
1. Global Banks Using Twitter for Banking:
Money can be sent using twitter accounts connected to Bank accounts, or it would have other options of receiving and sharing passcode and OTP with the receiver for authorizing a transaction.


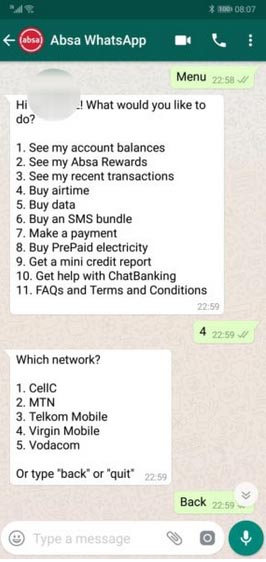
2. WhatsApp Banking service:
Absa Banking app (Africa) has introduced WhatsApp Banking to help customer receive updates or avail services via the WhatsApp messaging platform. On typing Help as a message, you can find out the full list of services available on WhatsApp. It is easy to use – simply type a keyword like or type the number against the service like “1” and follow the steps on screen.
3. CaixaBank Facebook Banking Application:
CaixaBank has launched a Facebook application that allows users to view their bank accounts and perform transactions via the social network. This is the first platform of its kind from a European bank, allowing customers to check account balances, make micro-donations and contract personalized card services. The new CaixaBank service for Facebook will also provide quick access to the bank’s primary online channel, Linea Abierta. Once activated, users can open the application via their personal profile or the bank’s Facebook page. Users will have to enter their Linea Abierta username and password each time the service is opened, as the service is located in a fully secure and private environment that can only be opened by each customer. At no time will Facebook have access to any personal or bank information.
Example: Australian Common Wealth bank using Facebook and other Banks using Messenger.

Organizational Risks Associated with Social Media Banking:
The Federal Financial Institutions Examination Council (FFIEC) specifically for these social media banking issues created the “Social Media: Consumer Compliance Risk Management Guidance”
Risk Areas for Social Media banking are as follows:
1. Compliance and Legal Risks
2. Reputation Risk
3. Operational Risk
Control: Financial institutions should consider the use of social media monitoring tools and techniques to identify heightened risk, and respond appropriately. Financial institutions should have appropriate policies in place to monitor and address in a timely manner the fraudulent use of the financial institution’s brand, such as through phishing or spoofing attacks.
Instances of Social Media Attacks and Breaches:
1. Phishing Direct Message Sent to Customers from Compromised Brand Account
Timeline: September 2011
Tactic: Account Takeover, Targeted Phishing & Malware
Summary: In September of 2011, an Australian bank suffered the worst-case scenario for an account takeover, in which attackers didn’t immediately vandalize the account or post inflammatory messages, but instead sent direct messages to followers asking them to disclose sensitive financial institutions. While most account hacks are merely embarrassing and costly from a brand and public relations perspective, they can also be used for large scale cyberattack against a brand’s most loyal and engaged followers.
2. Vevo Hacked Via Targeted LinkedIn Phishing Attack, 3.12TB Exfiltrated
Timeline: September 2017
Tactic: Targeted Phishing & Malware
Summary: Streaming service Vevo suffered a breach when one of its employees was phished via LinkedIn. Hackers were able to obtain and publicly release 3.12TB worth of the company’s sensitive internal data. The professional social network allows attackers to rapidly identify their target at a specific organization and send them a personalized message, all under the auspices of professional networking or recruitment.
3. Fake Social Media Persona Sends Malware to Employees Via Social Media
Timeline: July 2017
Tactic: Targeted Phishing/Malware, Fraudulent Accounts
Summary: Attackers created an incredibly compelling fake persona, a London-based photographer named Mia Ash, and connected with corporate employees. The attacker disseminated a Remote Access Trojan (RAT), called PupyRAT, via these social media honeypot accounts to hijack the controls of victims’ devices. The persona had accounts across several popular social networks.
4. 10k US Government Employees Spearphished with Malware-Laced Posts
Timeline: Early 2017
Tactic: Targeted Phishing/Malware, Fraudulent Accounts
Summary: In early 2017, Russian operatives sent over 10,000 custom phishing messages via social media, each link laced with malware enabling the attacker to access and control the victim’s device. This attack represents a major advancement in cyber capabilities and an escalation in Russia’s cyberwar against the US. This is the most well-organized, coordinated attack at the nation-state level we’ve ever seen.
5. 3rd Party App Leads to Hundreds of High-Profile Account Compromises
Timeline: March 2017
Tactic: Account Takeover
Summary: A vulnerability in a 3rd-party app called Twitter Counter allowed Turkish-language attackers to hijack controls of hundreds of high-profile accounts. They posted aggressive messages against the Netherlands after a contentious week of deteriorating relations between the Netherlands and Turkey and pivotal elections in both countries. The posts used swastikas and called the Dutch “nazis.” The breached accounts included a number of global brands and well-followed, verified accounts, including Forbes, the official Bitcoin Blockchain account, Starbucks, the European Parliament, UNICEF, Nike and Amnesty International.
6. Financial Crime Runs Rampant on Social Networks
Timeline: August 2016
Tactic: Fraud & Scams
Summary: ZeroFOX researchers revealed the vast underground world of financial crime on social media, in which scammers prey on the followers of verified banks with fraudulent financial services offerings, including card cracking and money flipping. The scale of the problem is massive, with nearly a quarter-million posts for a single type of scam on a single social network. The problem was found on every major social media channel and results in hundreds of millions of dollars in losses annually.
Conclusion:
Imagine if a cybercriminal blasted your 1000+ followers with a fake coupon (“2018/9 season 50% cashback for the next 30 minutes! #discount #Cashback #zerointerest #Zerodownpayment #football”) appended with the latest and greatest malware. Imagine the cataclysmic fallout of a cybercrime at the scale and speed of social media.
Social media banking is exposed to modern threat vector risks that can be reduced by implementing risk monitoring and remediation technology, security controls with compliance.
The most impactful attacks observed are third party apps compromised, targeted Phishing, malware, fraudulent accounts and the least impactful of social attacks, account takeovers, are often relatively harmless vandalism and trolling.
10 Best ways to reduce Risks Associated with Social Media Banking
1. Monitor social media and digital channels for business and security risks. Continuously watch for phishing links, fraudulent accounts, scams and more. A digital risk monitoring solution can be used for this purpose.
2. Ensure Multi-factor authentication is enabled.
3. Security professionals should train employees on what information should or should not be posted or visible to the public.
4. Work with marketing to gain access to social accounts and keep a close eye on social media initiatives and campaigns
5. Continuously monitor corporate social media accounts for cyber threats
6. Blacklist/block malicious URLs and IPs found on social media.
7. Establish workflow for dealing with social media cybercrime targeting the organization.
8. Take down malicious posts and profiles.
9. Test employees on susceptibility to social media cyberattacks.
10. Train employees on safe usage, best practices, and what to do in the event of an attack
Resources followed for the article:
- https://www.finextra.com/blogposting/13785/banking-on-social-media-platforms
- https://www.researchgate.net/publication/320142155_Social_media_banking_models_A_case_study_of_a_practical_implementation_in_banking_sector
- https://thefinancialbrand.com/35584/ffiec-social-media-regulations-guidelines-banking/all/
- https://www.zerofox.com/blog/social-media-security-best-practices/
- https://blog.hootsuite.com/social-media-security-for-business/
- FFIEC document for Risk Identified and management of risk using social media for Banking.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube








