SOC Compliance
SOC (Service Organization Control) is designed specifically to build trust and confidence in the service and products offered by the organizations to other service provider organizations
It focuses on a specific date and describes the procedures and controls that a service organization uses including the control systems test to determine if it’s been designed correctly.
It goes a step ahead and provides the service organization with an opportunity to report on its controls’ operating effectiveness over a period of time i.e. six months, in addition to the controls’ design.
SOC 2 – Addresses controls relevant to Security, Availability, Processing Integrity, Confidentiality and Privacy of the systems a service organization uses to process users’ data and the confidentiality and privacy of the information these systems process
It delivers a detailed report on the suitability of the design controls to a service organization’s system. Especially, SOC 2 Type 1 report is helpful to service companies as it assures the potential customers that the service organization has passed the said auditing procedure on the specified date and their data is safe with them.
This report provides a higher level of assurance than SOC 2 Type 1. The SOC 2 Type 2 reports describe the evidence of control measures taken and are evaluated for a minimum of six months to see if the systems and control are in place functioning, as reported by the management of the service organization.
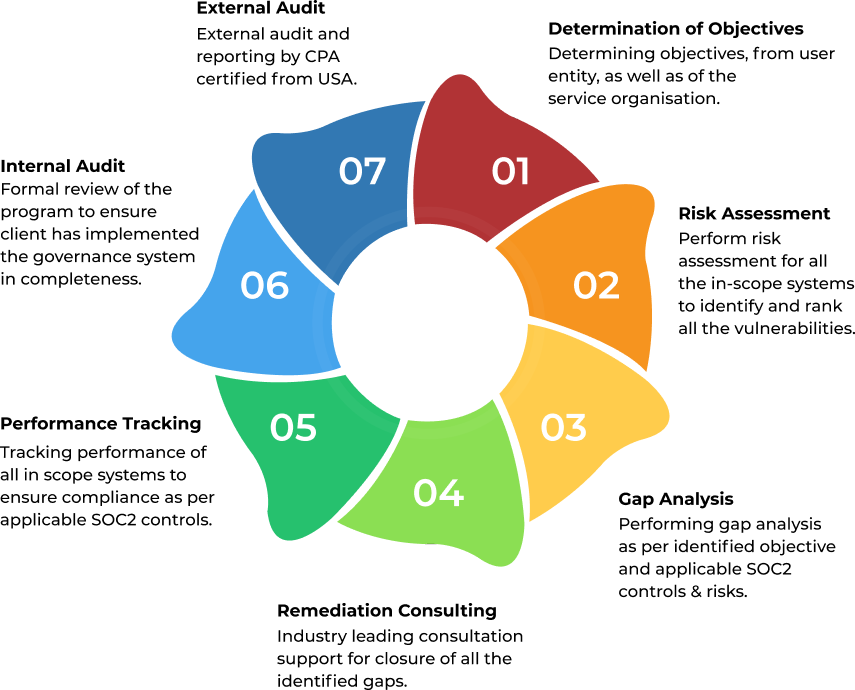

By performing a risk assessment, the auditor identifies the exact areas where the vulnerability risk is high and what measures should be implemented to control the upcoming threats.




As an industry leader in cyber security, SISA can help you understand your objectives, identifying gaps and threats, and can support you to remediate the gaps and risks in order to achieve a SOC Compliance report. With over a decade of experience in the financial and cyber security space, SISA acts as a trusted partner to over 2000 customers in 40+ countries to secure their network and technology infrastructure.
SISA has worked to provide cutting-edge compliance services to diverse industries and domains which include banks, ITES, insurance, e-commerce, payment service providers, telecommunications, airlines, and retail companies.

SISA is a Leader in Cybersecurity Solutions for the Digital Payment Industry. As a Global Payment Forensic Investigator of the PCI Security Standards Council, we leverage forensics insights into preventive, detective, and corrective security solutions, protecting 1,000+ organizations across 40+ countries from evolving cyberthreats.
Our suite of solutions from AI-driven compliance, advanced security testing, agentic detection/ response and learner focused-training has been honored with prestigious awards, including from Financial Express, DSCI-NASSCOM and The Economic Times.
With commitment to innovation, and pioneering advancements in Quantum Security, Hardware Security, and Cybersecurity for AI, SISA is shaping the future of cybersecurity through cutting-edge forensics research.

