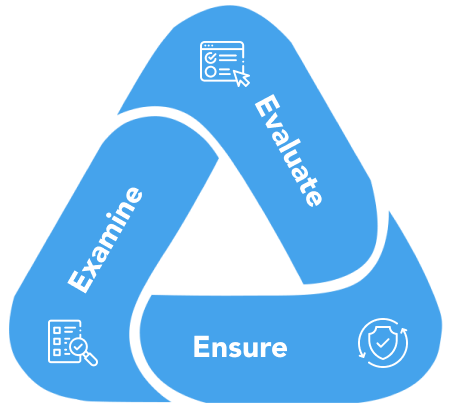
- EvaluateAssess applications against OWASP standards and Web Application Security Risks with in-house testing methodologies.
- Examine Conduct an in-depth analysis of back-end services, encryption protocols and source code, to assess effectiveness of controls.
- Ensure Adhere to best practices with both static and dynamic assessment of applications on the web, Android and iOS platforms.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global















 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube