Identifying Web Application Firewall in a Network

WAF (Web Application Firewall) plays an integral role in securing the Web Applications as WAF can mitigate risks and offers protection against a wide-range of vulnerabilities. This is why many organizations have implemented WAF solutions in their infrastructure. Implementation of web application firewall is just not the solution for resolving the security problems that a web-based applications might have, proper configuration is required in order to make the WAF capable of identifying and blocking many of the web-app attacks.
Before initiating a penetration test (Web Application engagement) a tester should be aware whether there are any WAF in place or not in the organizations infrastructure. Penetration can be done in two ways:
- White-box Testing: WAF presence should be questioned in the initial meetings with the client.
- Black-box Testing: Pen-tester should try on his own to identify whether there is any WAF in place or not.
This article explains on how to identify the presence of web application firewall while conducting web-app pen-test.
Manual Discovery of Web Application Firewall
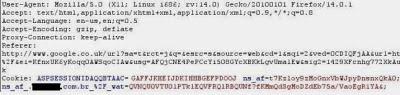
There are number of ways of identifying a WAF existence in a network. By checking the cookies we can get the indication of WAF as some of the WAFs add their own cookies in the communication between the client and the web server. In the below image, it is very clear that in a HTTP request a cookie has been added by the WAF. In the image ns_af clearly unveils that the WAF is a Citrix NetScaler App Firewall.
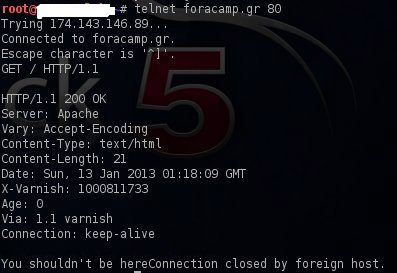
Another way is through the HTTP headers, as many WAF products make the web server to produce different HTTP responses from the generic ones after rewriting the header as these WAF products allows the header to be rewritten. As example we can see the below image as web server respond to the request with a message ‘You shouldn’t be here’ and unveiled that is Varnish
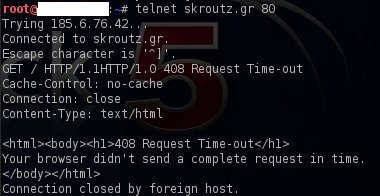
In addition to that, a Web Application Firewall presence can be easily identified in cases where the pen-tester tries to send a request and the session expires very quickly as shown in the below diagram.
Automated Discovery of Web Application Firewall
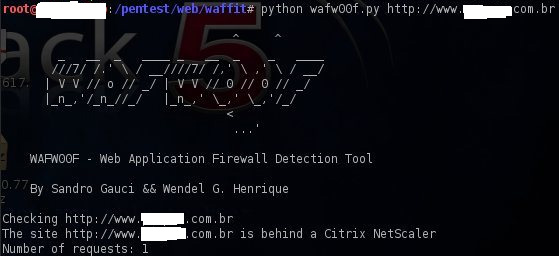
One of the well-known WAF Detection tool written by Mr. Sandro Gauci and Mr. Wendel G. Henrique Wiffit (Waf00f), it can detect and fingerprint WAFs. The best thing about this tool is that it is very simple to use and can discover a variety of WAF products (e.g. Profense, NetContinuum, Barracuda, Citrix NetScaler, ModSecurity, etc.) The below image shows the successful detection of a Citrix Netscaler firewall that protects the website.
Nmap can also be used for identifying the WAF presence as Nmap contains a script that can detect a web application firewall. After running the script against the same website as above and the results were the following:
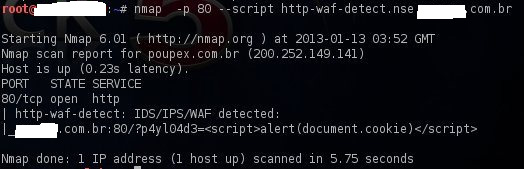
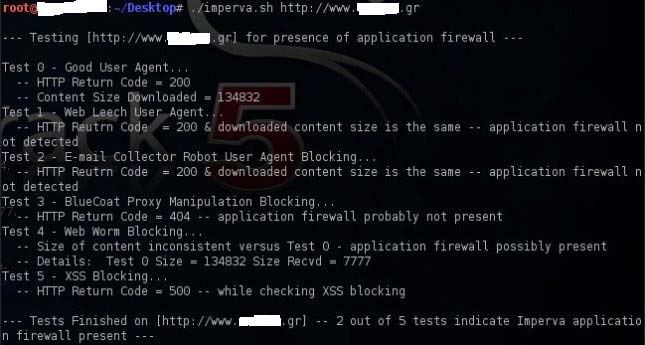
Lastly, showing the below image which shows that there is a script that is capable only to detect Imperva WAF installations.
Conclusion:
In this article we have tried to explain few of the techniques and tools used for detecting WAFs in the network while conducting web-application pen-test, so that the tester can modify the testing methodology accordingly.
This is one of the important and fundamental process that needs to be performed while doing any Web Application Penetration test during information gathering phase for ensuring that the results from the attacks that will be performed are accurate. After gaining this knowledge i.e. WAF is in place a penetration tester can try different techniques in order to bypass the protections provided by the WAF and exploit the weaknesses in the Web Application.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube