Internet of Things – The Changing Information Landscape

“Is it possible that a baby monitor can be used for spying?”
“Is our smart interactive TV keeping track of our viewing habits?”
“While we are driving to the office, is it possible that the car gets hacked?”
These questions may be new for us but the concept is an old one but let’s just accept the fact that who bothers about these things. Let them go…!!!

Source- http://www.pcworld.com/article/2103143/how-the-internet-of-things-opens-your-home-to-cyber-threats.html
This article is totally based upon our everyday usable objects but we never accept the fact that everything needs security .It may be possible that at the end of this article we might be cautious in using the daily objects which were reluctantly being used for so many years. But don’t worry, as a part of the security community we are trying to reduce the threats and vulnerabilities as much as possible.
Welcome to the world of “Internet of Things“. Keeping in mind “Everything is connected“.
Currently there are more objects connected to the internet as compared to the number of people in the world. The difference in scalar will continuously increase as more objects will gain the interface to the internet or in a different sense become physically accessible through the internet. Independent objects interaction as such is collectively coined the term “Internet of Things” (IoT).
The increase in mobility, heterogeneity, interoperability, population, complexity and distribution of components has given the attackers a plethora of surface to play with.
The past decade has shown a staggering bar in the increase of the devices that humans, as a consumer, use to directly interact with the network.
According to an article published on “The Guardian” there will be 40 billion IoT devices in 2025.
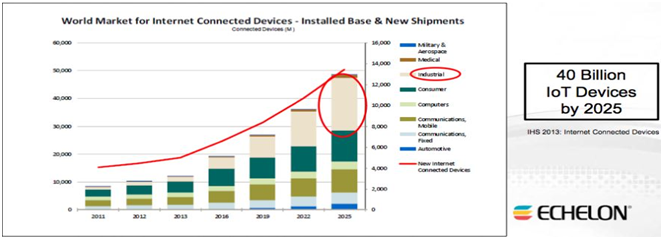
Source – https://www.theguardian.com/technology/blog/2013/nov/25/internet-of-things-connected-world
Taking a look on the other side of the picture there are also technologies that doesn’t require human interaction and which entirely survives on consuming more and more network information infrastructure.
There comes another clan of objects which are not directly connected to the internet but carries with them embedded information. For the identification purpose of IoT the best suitable way is the use of Radio Frequency Identification (RFID) tags. Objects may also possess embedded information in the form of Bar Codes, Serial Numbers and other forms of machine consumable object identifiers, burned on vast variety of objects involved.
For understanding the relationship between different IoT’s their statistical relationship needs to be identified and studied. As stated earlier, it’s expected that 40 billion IoT devices will be delivered in the market by 2025 and each person matched up with 6 connected devices, over 130 sensors and god knows how many embedded information objects.
Attack Vector
Nature of cyber-attacks will be upgraded significantly as IoT comes in picture because of the change in the operating environment. A structure needs to be set up for examining the threat outcomes of the IoT.
- Capture – System & Information
- Degrade, Disrupt, Deny and Destroy
- Manipulate
All these vectors are some common ones; we may see an updated list of it as the attack surface increases and believe me in just a blink of an eye its increasing 100 times or may be more than that.
Privacy Concerns in the evolutionary IoT
The vast variety of objects contributing to IoT will interact with humans as well as environment of the human by using all sorts of information that are deemed necessary as well as unnecessary. This perfect interconnection between the objects poses risk to the privacy and information leakage.
The IoT carries with it the work force of causing a significant amount of out of pocket losses for consumers as well as business. Taking reference from a study of SANS “Securing the Internet of Things Survey” gives a prediction that IoT infrastructure will see a tremendous request from healthcare or pharmaceutical industry. When compared with traditional IT systems, the incidents in such industries will carry physical, policy as well as financial impact e.g. Hacked defibrillators, deep-brain simulators etc.
One of the most contextual sensitive information is location. When GPS-enabled devices collect information about a particular entity, abundance of potentially sensitive data is generated and is made available to the application requesting. Controlling access to the information and providing individual requestors the appropriate level of granularity comes under the purview of privacy of location information. Compromise in any of the facets will affect the confidentiality of the information at its best.
Bored while running down the logical stuff?
Now let’s lay hands on some “Real World Facts and Threats”
First let’s just have a look at some top notch companies in this area. So, 10 most influential Internet of Thing companies
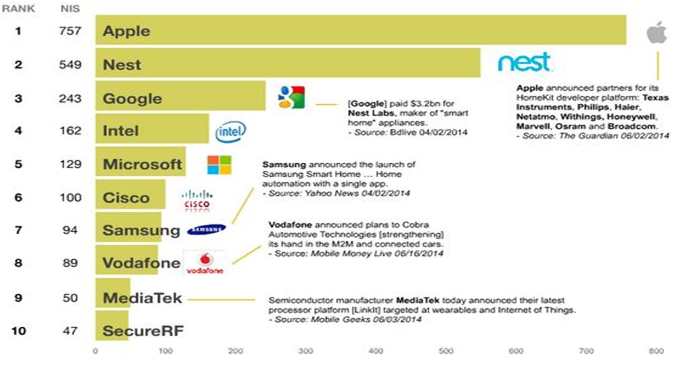
Source – https://www.cloudave.com/35202/companies-dominate-internet-things/
All these companies are working Head-to-toe for delivering the best secure services and that too in the most efficient manner but the problem takes birth from the genesis, which is software architecture. So, let’s discuss some of the newly discovered vulnerabilities and see that how much compromised are we.
Linux.Darlloz
It can be said that IoT is in its infancy stage but threats are evolving at a much faster pace. According to the report of Symantec, an investigator of their firm (Kaoru Hayashi) reported a worm that only targeted Linux OS.
Well, the worm Linux.Darlloz didn’t rang much bell at its initiation. It utilizes an old vulnerability of PHP, compromising the system and leaving a backdoor at last.
Since, the vulnerability is dependent upon an old version of PHP; to propagate further it needs an unpatched version of it. So, till now the worm doesn’t gain much attention according to the scenario given.
Now the investigators found some interesting facts:-
- It only targeted x86 chip architectures (found on personal computers and servers)
- Versions for the ARM, PPC, MIPS and MIPSEL chip architectures which were hosted on the same server as the original worm were discovered.
- The exciting fact was that, these architectures were generally found in:
- Home based routers
- Set-top boxes
- Security Cameras
- Pretty exciting stuff, isn’t it? But let’s, just don’t call it the end of the story and move further.
- The interesting facts haven’t finished yet, Linux.Darlloz scans for another Linux worm Linux.Aidra and if it finds any files associated with this malware, it immediately deletes them.
- No specific motive was found behind this but the inventor of Linux.Darlloz doesn’t want to share the limited amount of memory and processing power present in such household devices.
Good one!!
Now let’s give have a glimpse about the other worm too that was discussed above.
Linux.Aidra was more concerned with smaller devices, specifically cable and DSL modems. The worm exercise control over them and attaches them to a botnet which further facilitates in a DDoS.
Breach in Security Cameras
Recently US Federal Trade Commission (FTC) solved a case of TRENDnet. The firm deals in internet enabled security cameras and baby monitors. “
The cameras had faulty software that made them vulnerable for online viewing and if that person has the IP of that camera then he/she can even listen to the conversation over that as well.
The FTC over that even quoted “As a result of this failure, hundreds of consumers’ private camera feeds were made public on the internet.”
The notable factor was that none of the worms were responsible for this; it was simply a flaw of the security configuration.
Shodan
This search engine finds out devices which are internet enabled, devices include building heat control systems, water treatment plants, cars traffic lights, fatal heart monitors and power plant controls.
CHECKPOINTS for ALWAYS STAYING PROTECTED
- Perform a thorough audit of the devices you own, don’t go with the physical structure of it i.e. if a device doesn’t have a keyboard by no means it isn’t vulnerable.
- The devices connected to your home network are concurrently connected to the internet as well, so just make sure that they are secured enough.
- If you purchase a device that provides remote accessibility then disable it if isn’t needed.
- Change the default passwords to a unique value which only you know.
- Regularly check the manufacturer’s site for any update of the devices software.
So, just don’t start throwing off all the IP devices you have but make sure that EVERYTHING is SECURE, as we are living in an IoT environment.
—
References:
Report:
- SANS Health Care Cyberthreat Report
- Widespread Compromises Detected, Compliance Nightmare on Horizon
Research Paper:
- “Threat Implications of the Internet of Things”
By Michael J. Covington Security Intelligence Operations Cisco Systems, Inc. San Francisco, California, USA, Michael.Covington@cisco.com Rush Carskadden Security Austin, Texas, USA Rush@clicksecurity.com
Websites:
- http://www.pcworld.com/article/2103143/how-the-internet-of-things-opens-your-home-to-cyber-threats.html
- http://www.theguardian.com/technology/blog/2013/nov/25/internet-of-things-connected-world
- http://www.cloudave.com/35202/companies-dominate-internet-things/
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube








